AI
-

How to visualize the networks around you
Hello! In this post we’re going to shift gear onto a new topic: Wireless Hacking! When I was younger, I loved learning about networks. I was fascinated by all of the wireless traffic floating around through the air. This lead me down the rabbit hole of wireless hacking and among the very first wireless testing
-
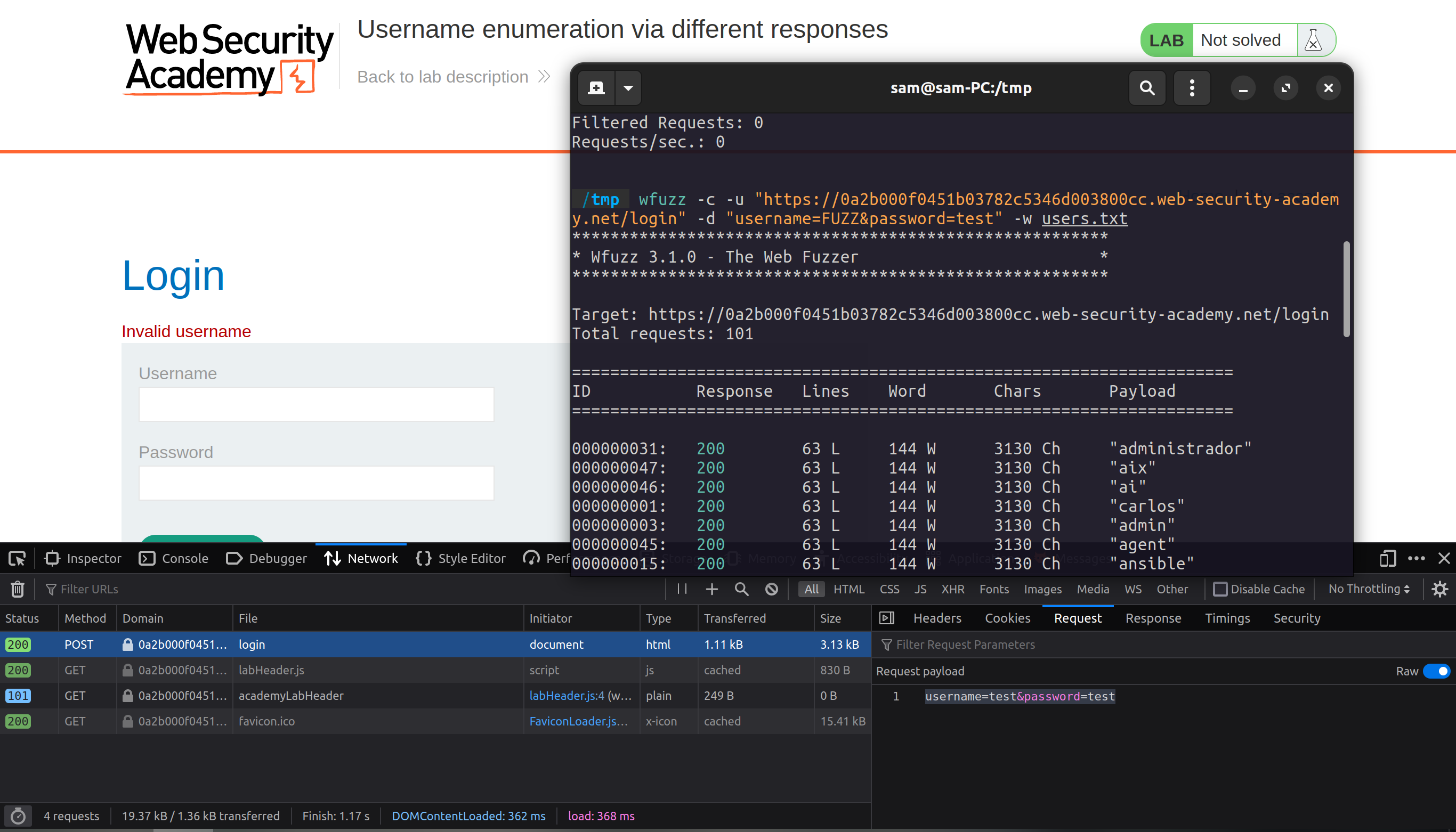
Harnessing the power of wfuzz for web hacking
In today’s post, I’ll introduce you to a tool that should be a part of every bug hunter’s toolkit, wfuzz! I use wfuzz in every bug bounty program I participate in. If you don’t know what wfuzz is, it’s a web application fuzzer. And if you haven’t heard of a web application fuzzer, they’re a
-

Unveiling my Methodology for Exciting Bug Discoveries and Optimal Results
When I first started getting into bug hunting, I tried to create the perfect methodology by mimicking what the greats were doing. I wanted to do recon and automation like Jason Haddix and become a command line guru like Tom Hudson. It was fun learning how to use tons of tools but I quickly became
-

How To Reverse Engineer API’s To Boost Your Bug Bounty Workflow
Recently, I’ve been working on APIsec University’s API Penetration Testing Course, where I’ve learned some invaluable methods of API hacking. One of the coolest things I’ve learned is how to effectively map out an API. So, in this post, I’m going to pass on what I’ve learned to you. Why waste time mapping an API?
-

My Bug Bounty Experience
Lately, I’ve been spending quite a bit of time learning web hacking and practicing what I’ve learned on bug bounty programs. For those of you unfamiliar with bug bounty programs, they are programs hosted by companies that provide payouts for vulnerabilities found on their platforms. Payouts vary depending on the criticality of the vulnerability and
-
Reflected DOM XSS Lab – Portswigger Web Academy
Lately, I’ve been participating in some bug bounty programs and have been doing Portswigger’s web security labs as a refresher. This lab was particularly interesting to me because it forced you to use dev-tools to debug the application to figure out where exactly to inject. So in the post, I’ll walk you through how to